Predictive behaviour models in the research of technology acceptance [Personality & TKMS series]
This is part 6 of a series of articles featuring edited portions of Dr. Maureen Sullivan’s PhD dissertation.
Predictive behaviour models are used by researchers to understand the beliefs, attitudes, and intentions towards technology adoption (acceptance), usage, and aversion.
Three common models used in the research of technology acceptance are:
Theory of reasoned action (TRA)
The technology acceptance model (TAM) originated from Fishbein and Ajzen‘s5 theory of reasoned action (TRA) and Ajzen and Fishbein‘s 6 theory of planned behavior (TPB). TRA shows that intentions of an individual‘s attitude and their subjective norms are the best prediction of the individual‘s actual behavior7 8. Furthermore, a subjective norm is the overall perception that others have regarding the relevance of what the individual should or should not do9 10.
In short, TRA is a predictive behavior model that is used to examine the factors that affect a person‘s intentions to perform or not to perform an action. Figure 1 shows the relationships of the TRA constructs. TRA can be applied in general settings to explain and predict behavioral intentions.
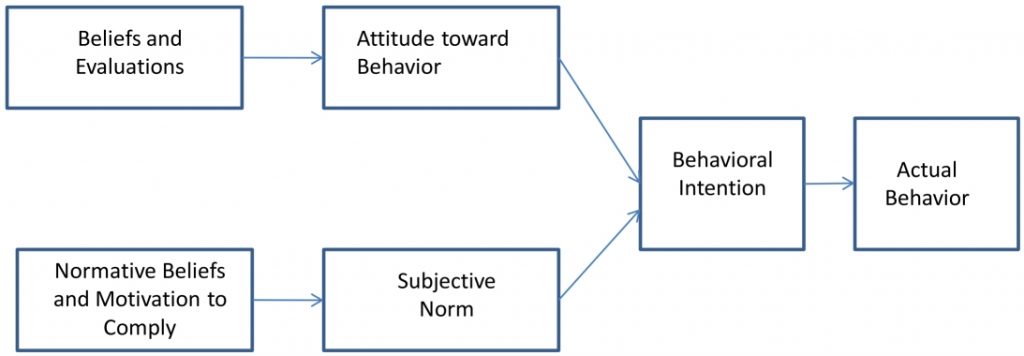
The three components that make up the TRA model are behavioral intention, attitude toward behavior, and subjective norm. Behavioral intention is the measurement of an individual‘s intention to perform a specific behavior11. Attitude toward behavior relates to an individual‘s feelings about performing a particular behavior12. Subjective norm is what an individual thinks about how others, that are important to them, think about the individual‘s decision to perform a particular behavior13 14. Overall, TRA hypothesizes that an individual‘s intention to perform or not to perform a behavior is based on an individual‘s attitude and subjective norm15 16.
Theory of planned behavior (TPB)
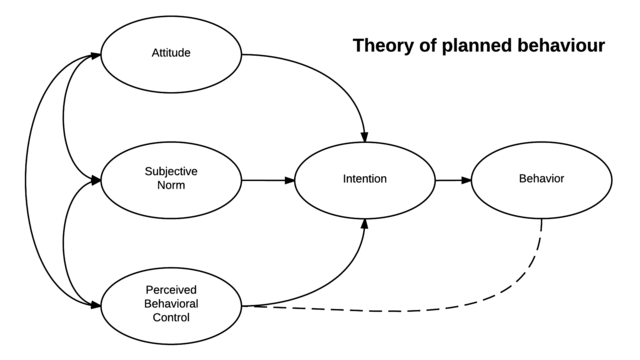
The theory of planned behavior (TPB) expands TRA by including another construct called perceived behavior control that was developed by Ajzen17 to account for a limitation found in the TRA that does not account for behaviors over which an individual has no voluntary control. Essentially, perceived behavior control is a behavior that an individual has no control over18. Furthermore, Luarn and Lin19 posited that the TPB says that an individual‘s attitude, subjective norms, and perceived behavior control directly influences that individual‘s behavioral intention to perform a particular behavior. Overall, in TPB, “behavior is a weighted function of intention and perceived behavior control, and intention is the weighted sum of the attitude, subjective norm, and perceived behavior control component” 20.
Technology acceptance model (TAM)
Davis‘s21 original research in the area of the technology acceptance model (TAM), resulted in the theory that the principal determinants of the intention to use computer systems are perceived effectiveness and perceived ease of use. Davis22 conducted additional research in TAM to address the determinants of behavioral intention in accepting and using technology and derived the latest TAM from the TRA model.
Thus, TAM is specific to IS behavior whereas TRA and TPB examine human behavior in general23. Information system researchers have examined, in support of TAM, the background utilization of perceived usefulness (PU) and perceived ease of use (PEOU), employing computer self-efficacy, perceived risk, training, and prior use24 25 26 27 28 29 30.
Davis‘s31 TAM model “did not include TRA‘s subjective norm as a determinant of behavioral intention because the subjective norm is one of the least understood aspects of TRA” 32. As a result, the subjective norm was not included in TAM because of its indeterminate abstract and psychometric status33.
Despite proving to be an effective tool for determining behavioral intentions to use IS, there are several limitations to the classical TAM model34. In fact, because of these limitations, several researchers modified and extended Davis‘s TAM model35 36 37. Many past TAM studies involving student participants using automation software or systems development applications and the resulting measurements reflected the differences in self-reported use and outlined a limitation in TAM38. Consequently, Legris et al.39 reported that researchers, like Lucas and Spitler40, believed that better results could be realized if the TAM processes were carried out in a business environment using business professionals or real customers as participants as well as using business process applications.
Another limitation of the classical TAM, as described by Legris et al., was that information systems (IS) are a separate issue in organizational activities. However, researchers Orlikowski and Debra-Hofman41 believed that, to be effective, the IS change process should rely on the relationship of the following: (a) the model used to manage the change, (b) technology, and (c) the organizational context.
In summary, past research has proven that the classical TAM is a useful theoretical model that can help to explain user behavior in IS implementation42 43. In fact, past empirical tests performed on TAM have proven that the tools used in these tests were found to be statistically reliable44 45 46 47 48. Overall, many researchers assert that TAM will continue to be an effective robust model and theoretical framework to predict IS usage49 50 51 52 53.
Next edition: Extended technology acceptance model (TAM2).
References:
- Fishbein, M., & Ajzen, M. (1975). Belief, attitude, intention & behavior. Reading, MA: Addison-Wesley Publishing. ↩
- Ajzen, I. (2005). Attitudes, personality and behavior (2nd ed.). NY: Open University Press. ↩
- Ajzen, I., & Fishbein, M. (1980). Understanding attitudes and predicting social behavior. Englewood Cliffs, NJ: Prentice-Hall. ↩
- Davis, F. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly, 13(3), 319-340. doi:10.2307/249008 ↩
- Fishbein, M., & Ajzen, M. (1975). Belief, attitude, intention & behavior. Reading, MA: Addison-Wesley Publishing. ↩
- Ajzen, I., & Fishbein, M. (1980). Understanding attitudes and predicting social behavior. Englewood Cliffs, NJ: Prentice-Hall. ↩
- Chan, S. C., & Lu, M. T. (2004). Understanding internet banking adoption and use behavior: A Hong Kong perspective. Journal of Global Information Management, 12(3), 21-43. doi:10.4018/jgim.2004070102 ↩
- Luarn, P., & Lin, H. H. (2005). Toward an understanding of the behavioural intention to use mobile banking. Computers in Human Behaviour, 21(6), 873-891. doi:10.1016/j.chb.2004.03.003 ↩
- Chan, S. C., & Lu, M. T. (2004). Understanding internet banking adoption and use behavior: A Hong Kong perspective. Journal of Global Information Management, 12(3), 21-43. doi:10.4018/jgim.2004070102 ↩
- Luarn, P., & Lin, H. H. (2005). Toward an understanding of the behavioural intention to use mobile banking. Computers in Human Behaviour, 21(6), 873-891. doi:10.1016/j.chb.2004.03.003 ↩
- Chan, S. C., & Lu, M. T. (2004). Understanding internet banking adoption and use behavior: A Hong Kong perspective. Journal of Global Information Management, 12(3), 21-43. doi:10.4018/jgim.2004070102 ↩
- Chan, S. C., & Lu, M. T. (2004). Understanding internet banking adoption and use behavior: A Hong Kong perspective. Journal of Global Information Management, 12(3), 21-43. doi:10.4018/jgim.2004070102 ↩
- Chan, S. C., & Lu, M. T. (2004). Understanding internet banking adoption and use behavior: A Hong Kong perspective. Journal of Global Information Management, 12(3), 21-43. doi:10.4018/jgim.2004070102 ↩
- Wang, Y., Wang, Y., Lin, H., & Tang, T. (2003). Determinants of user acceptance of Internet banking: An empirical study. International Journal of Service Industry Management, 14(5), 501-519. doi:10.1108/09564230310500192 ↩
- Chan, S. C., & Lu, M. T. (2004). Understanding internet banking adoption and use behavior: A Hong Kong perspective. Journal of Global Information Management, 12(3), 21-43. doi:10.4018/jgim.2004070102 ↩
- Wang, Y., Wang, Y., Lin, H., & Tang, T. (2003). Determinants of user acceptance of Internet banking: An empirical study. International Journal of Service Industry Management, 14(5), 501-519. doi:10.1108/09564230310500192 ↩
- Ajzen, I. (1991). The theory of planned behavior. Organizational Behavior and Human Decision Processes, 50, 179-211. doi: 10.1016/0749-5978(91)90020-T ↩
- Luarn, P., & Lin, H. H. (2005). Toward an understanding of the behavioural intention to use mobile banking. Computers in Human Behaviour, 21(6), 873-891.
doi:10.1016/j.chb.2004.03.003 ↩ - Luarn, P., & Lin, H. H. (2005). Toward an understanding of the behavioural intention to use mobile banking. Computers in Human Behaviour, 21(6), 873-891. doi:10.1016/j.chb.2004.03.003 ↩
- Taylor, S., & Todd, P. A. (1995). Understanding information technology usage: A test of competing models. Information Systems Research, 6(2), 144-176. doi:10.1287/isre.6.2.144 ↩
- Davis, F. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly, 13(3), 319-340. doi:10.2307/249008 ↩
- Davis, F. D. (1993). User acceptance of information technology system characteristics, user perceptions and behavioral impacts. Int’l Journal of Man-Machine Studies, 38(3), 475-487. doi:10.1006/imms.1993.1022 ↩
- Luarn, P., & Lin, H. H. (2005). Toward an understanding of the behavioural intention to use mobile banking. Computers in Human Behaviour, 21(6), 873-891. doi:10.1016/j.chb.2004.03.003 ↩
- Chan, S. C., & Lu, M. T. (2004). Understanding internet banking adoption and use behavior: A Hong Kong perspective. Journal of Global Information Management, 12(3), 21-43. doi:10.4018/jgim.2004070102 ↩
- Gefen, D., Karahanna, E., & Straub, D. (2003). Trust and TAM in online shopping: An integrated model. MIS Quarterly, 27(1), 51-90. ↩
- Legris, P., Ingham, J., & Collerette, P. (2003). Why do people use information technology? A critical review of the technology acceptance model. Information and Management, 40(3), 191-204. doi:10.1016/S0378-7206(01)00143-4 ↩
- Lu, J., Yao, J. E., & Yu, C. S. (2005). Personal innovativeness, social influences and adoption of wireless internet services via mobile technology. The Journal of Strategic Information Systems, 14(3), 245-268. doi:10.1016/j.jsis.2005.07.003 ↩
- Venkatesh, V., & Davis, F. D. (2000). A theoretical extension of the technology acceptance model: Four longitudinal field studies. Management Science, 46(2), 186-204. doi:10.1287/mnsc.46.2.186.11926 ↩
- Venkatesh, V., Morris, M. G., Davis, G. B., & Davis, F. D. (2003). User acceptance of information technology: Toward a unified view. MIS Quarterly, 27(3), 425-478. ↩
- Wang, Y., Wang, Y., Lin, H., & Tang, T. (2003). Determinants of user acceptance of Internet banking: An empirical study. International Journal of Service Industry Management, 14(5), 501-519. doi:10.1108/09564230310500192 ↩
- Davis, F. D. (1993). User acceptance of information technology system characteristics, user perceptions and behavioral impacts. Int’l Journal of Man-Machine Studies, 38(3), 475-487. doi:10.1006/imms.1993.1022 ↩
- Fishbein, M., & Ajzen, M. (1975). Belief, attitude, intention & behavior. Reading, MA: Addison-Wesley Publishing. ↩
- Davis, F. D., Bagozzi, R. P., & Warshaw, P. R. (1989). User acceptance of computer technology: A comparison of two theoretical models. Management Science, 35(8), 982-1003. doi:10.1287/mnsc.35.8.982 ↩
- Legris, P., Ingham, J., & Collerette, P. (2003). Why do people use information technology? A critical review of the technology acceptance model. Information and Management, 40(3), 191-204. doi:10.1016/S0378-7206(01)00143-4 ↩
- Adams, D. A., Nelson, R. R., & Todd, P. A. (1992). Perceived usefulness, ease of use, and usage of information technology: A replication. MIS Quarterly, 16(2), 227-247. ↩
- Jackson, C., Chow, S., & Leitch, R. (1997). Toward an understanding of the behavioral intention to use an information system. Decision Sciences, 28(8), 357-389. ↩
- Venkatesh, V., & Davis, F. D. (1996). A model of the antecedents of perceived ease of use: Development and test. Decision Sciences, 27(3), 451-481. doi:10.1111/j.1540-5915.1996.tb00860.x ↩
- Legris, P., Ingham, J., & Collerette, P. (2003). Why do people use information technology? A critical review of the technology acceptance model. Information and Management, 40(3), 191-204. doi:10.1016/S0378-7206(01)00143-4 ↩
- Legris, P., Ingham, J., & Collerette, P. (2003). Why do people use information technology? A critical review of the technology acceptance model. Information and Management, 40(3), 191-204. doi:10.1016/S0378-7206(01)00143-4 ↩
- Lucas, H. C., & Spitler, V. K. (1999). Technology use and performance: A field study of broker workstations. Decisions Sciences, 30(2), 291–311. doi:10.1111/j.1540-5915.1999.tb01611.x ↩
- Orlikowski, W. J., & Debra-Hofman, J. (1997). An improvisational model for change management: The case of groupware technologies. Sloan Management Review, 38(2), 11-21. ↩
- Gefen, D., Karahanna, E., & Straub, D. (2003). Trust and TAM in online shopping: An integrated model. MIS Quarterly, 27(1), 51-90. ↩
- Legris, P., Ingham, J., & Collerette, P. (2003). Why do people use information technology? A critical review of the technology acceptance model. Information and Management, 40(3), 191-204. doi:10.1016/S0378-7206(01)00143-4 ↩
- Adams, D. A., Nelson, R. R., & Todd, P. A. (1992). Perceived usefulness, ease of use, and usage of information technology: A replication. MIS Quarterly, 16(2), 227-247. ↩
- Davis, F. D., Bagozzi, R. P., & Warshaw, P. R. (1989). User acceptance of computer technology: A comparison of two theoretical models. Management Science, 35(8), 982-1003. doi:10.1287/mnsc.35.8.982 ↩
- Legris, P., Ingham, J., & Collerette, P. (2003). Why do people use information technology? A critical review of the technology acceptance model. Information and Management, 40(3), 191-204. doi:10.1016/S0378-7206(01)00143-4 ↩
- Venkatesh, V., & Davis, F. D. (1996). A model of the antecedents of perceived ease of use: Development and test. Decision Sciences, 27(3), 451-481. doi:10.1111/j.1540-5915.1996.tb00860.x ↩
- Venkatesh, V., Morris, M. G., Davis, G. B., & Davis, F. D. (2003). User acceptance of information technology: Toward a unified view. MIS Quarterly, 27(3), 425-478. ↩
- Davis, F. D., Bagozzi, R. P., & Warshaw, P. R. (1989). User acceptance of computer technology: A comparison of two theoretical models. Management Science, 35(8), 982-1003. doi:10.1287/mnsc.35.8.982 ↩
- Gefen, D., Karahanna, E., & Straub, D. (2003). Trust and TAM in online shopping: An integrated model. MIS Quarterly, 27(1), 51-90. ↩
- King, W. R., & He, J. (2006). A meta-analysis of the technology acceptance model. Information & Management, 43(6), 740-755. doi:10.1016/j.im.2006.05.003 ↩
- Legris, P., Ingham, J., & Collerette, P. (2003). Why do people use information technology? A critical review of the technology acceptance model. Information and Management, 40(3), 191-204. doi:10.1016/S0378-7206(01)00143-4 ↩
- Venkatesh, V., Morris, M. G., Davis, G. B., & Davis, F. D. (2003). User acceptance of information technology: Toward a unified view. MIS Quarterly, 27(3), 425-478. ↩